At the beginning of the Internet Era, we were so hypnotized by the allure of going online that the idea of needing to secure our networks and data against evil-doers (thank you, George Bush II, for that wonderful slang) never crossed our minds.
But it didn’t take long to realize there were deviants out there called hackers. These hackers specialize in finding us online, stealing our information, and creating chaos. At first, it didn’t seem like their mischief was based on profit as much as, well, mischief for its own sake.
But once they realized there was money to be made by nefarious activity online, the instances of attempted (and successful) hacks skyrocketed.

A quarter of a century after the public wandered online in large numbers, hacking is now all about profit. Whether it’s conducting a database smash-and-grab to sell personal financial information on the Dark Web or shutting down a website with ransomware until a bounty is paid, hackers have forced the good guys to play a button-down defense or suffer the consequences.
What is cybersecurity?
Think of it like this. One part is the strategy involved in protecting an internet-connected internal network (data, hardware, software) from outside penetration. The goal of individuals and companies is to deploy security measures to thwart malicious outside attempts to access, alter, delete, destroy, or extort systems and data.
The second part of any cybersecurity strategy is to create a safe environment to go online and do what you want or need to do without fear of being compromised and allowing one of those evil-doers into your systems.
When it comes to understanding cybersecurity, we focus on three actors - the attacks, the attacker, and the attacked. This is known in the industry as the Cybersecurity Trifecta.
Statistics on the Different Threats and Types of Attack
It’s easy to think about a hack as being similar to a bank robbery, where the evil-doers show up waving guns and demanding cash. The whole thing is over within a few minutes. This is not often the case with a hack.
A successful hacking operation might unfold over days or even months and in well-defined stages. It’s the ultimate exercise in patience. Each stage moves the hacker closer to the final goal. Along the way, additional attacks might be added, each with a specific purpose that leads toward the final goal, whether it be profit, chaos, or something different.
This is not to say that a successful hack is always slow and deliberate, though often it is. For giggles, check out this blow-by-blow description of how one dude lost $3,000 overnight from his Bitcoin account.
As you can see from that Verge article, there were several steps along the way to achieve the final theft:
- The email address was compromised and a new burner phone number and backup email address were attached to it.
- The phone password is reset and calls are forwarded to the burner phone.
- Google account and 2FA (two-factor authentication), including confirmation codes, are taken over.
- Resetting the Coinbase account and transferring the balance of $3,600 to a burner account.
- Made three separate withdrawals that night, spaced 30 minutes apart.
- The money went into a series of dummy accounts that covered the heist.
Each step along the way was engineered by a different method of attack, but all moved closer to the final goal of stealing the victim’s Bitcoin. Keep reading, and we’ll learn more about the first part of the cybersecurity trifecta - the attack.
Deploying Malware
The word “malware” is a shortened form of “malicious software”. It is simply a program designed to be inserted into a user’s computer to disrupt or damage the device or network.
Hackers also use malware to let themselves inside the victim’s system to control it or even shut it down. Some common types of malware you might have heard of include viruses, worms, Trojans, spyware, etc. There are many more.
All of the following online threats fall under the overall category of malware. Though the mass public only began using the internet in the mid-1990s, the first ever malware incident occurred all the way back in 1971 and was dubbed “The Creeper.” This malware was identified as a virus, but some experts said it acted like a worm.
Regardless, The Creeper will live forever in infamy as the first malware.
Adware
Adware is exactly what the name suggests. This type of malware downloads itself into a target computer and displays advertising or marketing material without permission. Trying to clean it up can be a mess after your computer is infected.
The use of adware has increased significantly in recent years. It accounts for 72% of all malware found on mobile phones and increased by 38% from 2019 to 2020 alone. You might be curious about what the remaining 28% of mobile malware is:
- Banking trojans
- Fake apps
- Lockers
- Downloaders
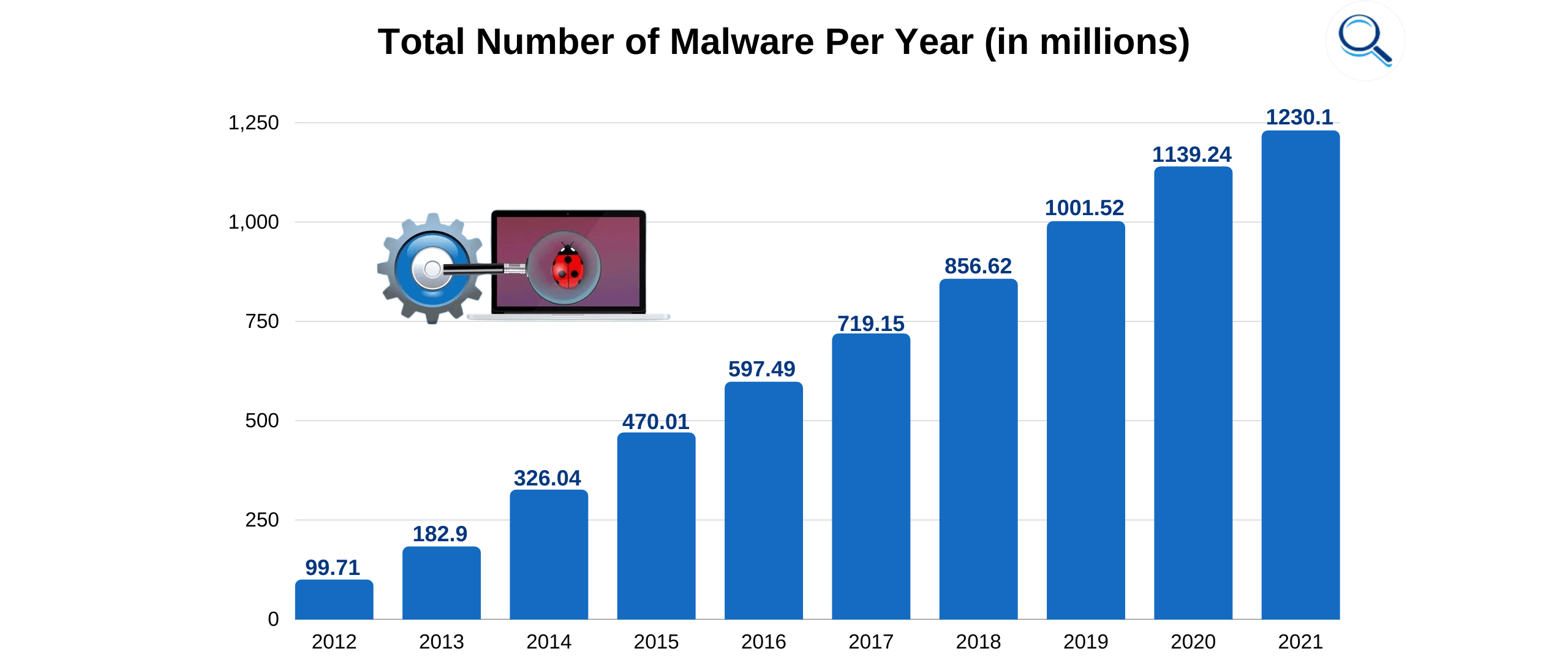
How much malware is there overall? In short, a lot. More than one billion separate malware programs are circulating online, and the stuff spreads like an actual disease. The AV-Test Institute reports almost half a million new instances of malware to appear daily. More than 17 million are registered each month.
Though adware seemed to hit its peak in the early 2000s (before adware blockers became a thing), the Covid pandemic has seen a renaissance of sorts with this type of nasty program. The security company Kaspersky has identified more than 120,000 different adware programs in the wild, pretending they are online conferencing software like Zoom.
You think you’re downloading a legitimate program in order to fulfill the tasks of your new remote job, and - whammo - your device is infected with ads that just won’t stop.
Malwarebytes reported a 463% adware growth in a single year alone. Windows systems were hit with 24 million instances and Mac with 30 million. In passing the former, that last number has been a surprise for the reputation of the vaunted Mac security.
Our final bit of advice about adware is this. If your computer or phone suddenly starts throwing out popup ads and sending you to websites you never asked it to, there’s a good chance you have an adware infection.
The good news is that there is a horde of “good guy” internet experts trained in the fine art of adware removal. If you don’t have a clue where to start, ask your local computer store for a recommendation.
Viruses
We’ve mentioned the world’s first malware known as The Creeper. This virus was literally the granddaddy of internet attacks. Probably more than any other specific malware or online threat, everyone who goes online (and probably some who don’t) have heard the word virus associated with the internet. This transcendent technical term conjures visions of a destructive force set loose in whatever device you want to imagine - desktop, laptop, mobile phone, tablet, gaming system, etc.
The interesting thing about a computer virus is that it cannot replicate without human interaction. A virus can spread when we click a link, open an attachment, launch an application, or download a file. Luckily for the survival and spread of viruses everywhere, humans have shown an amazing willingness to do all four of these actions with regularity.
In fact, releasing a virus by launching an application when you click an executable (.exe) file is still the most popular way to spread them at 53%. A follow-up statistic shows us that including an executable file in an email is a hacker’s favorite choice 46% of the time.
We’ve mentioned the world’s first virus, but what about the weirdest? That honor goes to the 2009 ILOVEYOU virus, which, once released, went to work renaming all files to “iloveyou” until the system crashed. Estimates say that a full 10% of PCs around the world were eventually infected. Damage estimates ran as high as $15 billion.
But that wasn’t even the most expensive virus. Take a look at the top five.
- MyDoom - $38 billion
- So Big - $37 billion
- ILOVEYOU - $15 billion
- Conficker - $9 billion
- Code Red - $2 billion
Considering these numbers, it’s probably no surprise that 32% of the world’s computers are infected with some kind of virus. If you find yourself in this unfortunate company, what should you do?
The bottom line is that if your computer or phone is doing fine and then suddenly acts funky, the odds are at least decent that you have acquired a virus. Now what? Here’s the short version.
- Download and install a virus scanner
- Disconnect from the internet
- Reboot the computer into safe mode and delete temporary files
- Run a virus scan and delete or quarantine the virus
- Reboot the computer and change all passwords
- Update all software, browser, and OS to the newest versions
Oh yeah. If you aren’t using anti-virus software, start doing it.
Worms
We just mentioned how a computer virus requires human interaction in order to spread. We’re sure you’ll be overjoyed to learn that a worm is not so needy. As a subset of the Trojan horse malware, worms can propagate or self-replicate once a system is initially breached.
No humans needed.
If this is starting to sound like an apocalyptic science fiction movie in which the computers take over, you’re right. A virus requires a host program to multiply, but a worm does not. Think of it as an independent program that plans its own attacks. So far, worms don’t run the world, but who’s to say they won’t eventually?
The world's first worm is generally acknowledged as The Creeper, which we’ve already mentioned. Some call it a virus, and some call it a worm. Regardless, the second worm ever, Reaper, was created to root out and kill the first.
In 1988, a computer science graduate student by the name of Robert Morris couldn’t help himself. He turned loose a worm that ultimately infected around 10% of computers online at that time. Unfortunately for Morris, he became the first person tried and convicted under the Computer Fraud and Abuse Act, which had been enacted a few years prior.
The court estimated the cost of recovering from Morris’ worm attack to be from $200 to $53,000 per installation.
Fast forward a couple of decades, and we have another high-profile worm called Stuxnet. Unlike our first examples, Stuxnet was not the result of academician experimentation. This one was created by the US and Israeli governments working together.
This early battle in an ensuing cyber-war against Iran’s nuclear program was responsible for crashing 984 centrifuges between 2008 and 2012 and likely set back Iranian efforts to develop nuclear weapons by two years.
So, how do computer worms get into the wild? Let’s look at the example of the Storm Worm, which launched in 2007 and propagated over the next decade. Estimates say around 1.2 billion emails were sent with the goal of creating a botnet that would then be used to target and take down popular sites.
As many as one million computers infected with the Storm Worm are still part of the envisioned botnet and don’t know it.
Then there was the worm called SQL Slammer in 2003. Its creators displayed out-of-the-box thinking when they sent the program out to a list of randomly generated IP addresses and ended up infecting 75,000 computers.
It’s difficult to estimate how many worms are online today due to it being hard to differentiate them from a virus. There are even virus/worm hybrids out there to complicate matters further. The bottom line is that worms are dangerous for the precise reason that defines them - they don’t need a host to spread.
What is your best plan for dealing with a worm in your computer? Don’t let it get there in the first place. Treatment for a worm infection is similar to what we described for a virus. The important thing is to ensure your machine is disconnected from the internet and any local networks before taking remedial steps.
Trojans
You have to go a long way back to find the first reference to a Trojan horse. Classic literature (Aeneid by Virgil and the Odyssey by Homer). Long story short - around 33 centuries ago, the ancient Greeks built a huge wooden horse to trick their enemies in the city of Troy. Since a siege hadn’t helped them gain entrance, they pretended the horse was a gift.
Troy brought the horse inside the city gates, which was a big mistake. Inside were hidden soldiers. That night, the soldiers came out and let the rest of the Greek army inside. It turned out to be a bad day for Troy.
Knowing this bit of history makes it clearer why the type of malware that looks legitimate but isn’t is called a Trojan horse in modern parlance. Trojan malware is typically introduced via social engineering that encourages a victim to unwittingly introduce it to their system as an email attachment or download a “free to use” file.
Some people refer to a Trojan as a virus, but that’s not exactly accurate. A virus is able to self-execute and replicate, while a Trojan requires a human to take proactive action to get it started.
Once downloaded in the host system, the Trojan goes to work executing whatever nasty task its inventor programmed into it. Trojan malware has become highly used and effective in recent years. In fact, Firewall Times suggests Trojan attacks comprise 51% of all malware.
Trojans contribute to the popularity of email as an attack vector. Despite the persistent idea that email is an outdated mode of online communication, 92% of malware attacks use email to introduce infection to a system. This is where social engineering comes in since there is no way to complete a Trojan attack unless the victim takes action, such as opening an attachment or clicking on a link that takes them to a malicious site.
Many people wrongly assume that a Trojan or other type of malware infects a system and is discovered and removed. The astounding statistic is that - while this is the typical process - the dwell time (time from infection to discovery) is measured in years or around 798 days.
We’ll wait while you pick your brain up off the floor. That is a long frickin’ time. Imagine how much damage a hacker can do in this more than two-year stretch. Would you invent a bad guy into your house and let him roam around doing his worst for two years plus? Hopefully not.
This is why cybersecurity experts highly recommend anti-virus and anti-malware protection, as well as a VPN.
Guess what? We just lied to you. Let us explain. That insanely high dwell time we just mentioned has declined to only 24 days in recent years due to the rise of ransomware. It has been a change in the thought processes of hackers. Ransomware is useless unless the victim knows it is there so they can pay (or not) the hacker’s demand.
We’ll talk about ransomware more in a minute, but for now, just be aware that it has significantly affected the malware industry and online security.
Trojan malware first appeared as legitimate software in the mid-1970s. By the late 1980s, things had turned to the dark side, and many malicious programs were making the online rounds, including the first-ever example of ransomware known as AIDS.
The most popular types of Trojans are:
- Backdoor
- Downloader
- Distributed denial-of-service
- Banking
- Fake antivirus
Trojan attacks can leave behind a lot of damage. For example, in 2010, a yucky Trojan was released in the Eastern European region. Named Zeuss or Zbot, it eventually helped its makers abscond with around $70 million.
How do you get a Trojan off your device? Luckily, this type of malware doesn’t self-replicate and is, therefore, less dangerous to set off a large-scale incident. Most anti-virus packages come with Trojan removal capability. As with some of the previous malware we’ve mentioned, disconnect the computer from the internet, scan for the Trojan, and then either delete or quarantine it.
Bots
The very science-fictiony term “bots” is short for “internet robot”. You might also hear them referred to as spiders, crawlers, or web bots. Google uses bots in the form of crawlers to constantly update its search engine. Hackers love to use the same technology as malware, allowing a hacker to control a computer or network.

Some of the nefarious activities you can send a bot out to do are:
- Gather passwords
- Log keystrokes
- Steal financial information
- Relay spam
- Capture and analyze packets
- Launch DoS attacks
- Open backdoors to an infected computer
- Exploit backdoors created by other malware
Usually, a bot is put to work as part of a botnet that infects a large number of computers. In this type of attack, each bot penetrates a single computer and reports back to a central command server. The person controlling the central server also controls each bot and, therefore, each infected computer.
Here are the most common malicious bots in use today.
As you can see, the aptly-named Trickbot is the most popular bot, accounting for almost a third (29%) of all bots in existence. Trickbot is also a Trojan. It was developed by a cyber-crime family who has turned it into an expansive modular malware ecosystem with alleged ties to Russian intelligence.
Botnet used by hackers is a growing trend. The last quarter of 2021 saw a rise of 23% in the use of bots for coordinated command and control-style attacks. The gross number for that quarter was 3,271.
Distributed Denial of Service (DDoS) attacks commonly use bots in a coordinated large-scale attack intended to overwhelm target servers. The first half of 2021 saw a mind-boggling 5.4 million of these kinds of attacks launched, which was an increase of 11% year-on-year.
Unsurprisingly, the financial sector finds itself the one most often under bot attack. Additionally, 60% of botnet activity is aimed at stealing user login credentials.
Right now, bots are big business as one of the top malware types in the hacker universe.
But before we leave the bot topic, we’d like to touch on one use that can actually be helpful - the ubiquitous chatbot. Love ‘em or hate ‘em, they are here to stay. These AI-powered bits of software are front and center on 23% of customer service sites, and a full 80% of people have interacted with them to some extent.
A chatbot’s job is to ask a few questions that either solve your issue or let them route you to a human representative who can help you out. With chatbots handling full conversations around 69% of the time, the cost savings to a company can be substantial.
Ransomware
One of the undoubted malware leaders these days is ransomware. What is it exactly? The basic idea is to introduce a malicious software package into a target computer or network that threatens the data held there unless a ransom is paid, often in untraceable cryptocurrency like Bitcoin.
Based on the field of crypto virology, a ransomware infection can take a few different routes.
- The software may simply lock you out of your files
- Or it might encrypt your files, making them unreadable unless you have the decrypt key
Ransomware attacks have taken over news headlines in recent years as they have targeted local governments, schools, universities, and other public facilities that have a hard time operating without access to their data.
The latest numbers show there is a ransomware attack every 11 seconds. Only a fraction are successful, but the annual losses are up to about $20 billion.
Businesses are a big target because, like public facilities, they need their data to function. Attacks targeted at businesses go out about every 40 seconds. Like other types of malware that depend on social engineering for success, two-thirds of ransomware infections were introduced by a hacker’s successful email phishing.
Criminals reap about $1 billion in combined revenue from successful ransomware demands. To date, about 9% of Americans have found themselves entangled in a ransomware attack either personally or through an organization they are associated with.
What is the best way to avoid ransomware? It can be pretty simple. Never click on a link or download a file in an email unless you are super extra sure it is legitimate. Hackers rely on a willing and gullible public to succeed. That’s why 46% of ransomware attacks come from someone in authority, like the FBI or the IRS.
This tactic is squarely intended to scare you into stupid-clicking. Keep your cool. Don’t click. Make a phone call to the alleged organization that reached out to you. Nothing is going to happen in the next five minutes that a random email click will solve.
Spyware
This type of malware is pretty self-explanatory. It is designed to sneak into a host computer and quietly send information back to its owner. Its goal is to stay hidden while tracking and recording your online activity. It knows everything you enter, upload, download, or store.
Like many of the other members of this list, spyware is a form of malware with a few distinguishing characteristics. For one thing, it doesn’t replicate like some malware. It also doesn’t do any damage to your system. It just sits there, hidden in the background, recording everything that happens. There’s a good chance you won’t even know it’s there.
To confirm the sneaky nature of spyware, consider the following:
- 80% of all internet users are affected by spyware to some extent
- 89% of these have no idea spyware is watching them
- 95% of these never gave permission for the program to be installed
How do you get spyware? There are a variety of ways a dedicated hacker with a spyware package can compromise your device or system, but most are a result of security vulnerabilities related to bugs in legitimate software and backdoors created by other malware attacks.
Coding mistakes happen, and spyware is often there to take advantage of them.
While spyware is a major inconvenience to individuals, it might be even worse for businesses. For small and medium-sized businesses, dealing with spyware represents around 40% of their overall security costs related to downtime.
Large corporations lose about 2.2% ($30 million) of their annual income to spyware-related costs. This is no small matter.
Spyware often finds its way onto your device via what you think is a legitimate third-party app. That was the case with the PhoneSpy app in 2021. Hackers slipped the spyware into 23 legitimate-looking apps and infected over 1,000 Android devices. In other words, this malicious software was literally downloaded onto the victim’s computer on purpose.
It should be noted that none of these apps were listed in the Google Play Store. This should be your very first criterion when deciding what to download and install on your system. Leave it alone if it’s not listed in one of the major app stores!
Spyware can be a tricky little bugger to remove but typically, a combination of anti-spyware software, anti-virus software, and HijackThis (a free, open-source tool) will get the job done.
Cryptojacking Malware
Since it is directly related to cryptocurrency, cryptojacking malware has only been in the general vocabulary for about five years. The idea is based on how a cryptocurrency - Bitcoin is a good example - rewards anyone who lends computing power to help process transactions.
It can be a profitable undertaking but requires a lot of computing power. Enterprising cyber miners soon realized they could place a bit of malware on someone’s computer without their knowledge and essentially borrow that computing power for profit.
Obviously, there’s an ethical problem with this which has led to the practice being called cryptojacking. Though the malware used in these sorts of attacks can and has been deployed on a variety of cryptocurrencies, we’ll focus on Bitcoin since it has shown itself to be the most popular and profitable.
Bitcoin has fluctuated in value from its humble beginnings of fractions of less than a penny per coin to almost $70,000 in October of 2021 and now has settled back into the $20,000 range. It starts to make sense why there is so much interest in cryptomining and, by extension, cryptojacking.
When the largest cryptojacking operation went belly up in 2019, everyone thought interest in the practice would subside. Silly experts. That is exactly what didn’t happen. When the 2021 SonicWall Cyber Threat Report was released, it revealed more than 15 million cryptojacking attacks. Year-on-year monthly increases ranged from 100% to a whopping 1,400%.
Released in the middle of the year, the SonicWall report cited 51 million cryptojacking attacks thus far, a 23% increase from the previous year.
North America has become a hotbed for cryptojacking, with a 280% increase, while Asian attacks actually dropped by 87%.
How do you know if you’ve been cryptojacked? One sign is if you start having mysterious performance issues. Cryptojacking puts a load on your computer’s processing speed, so programs, apps, and browsing will slow way down.
If we could leave you with one bit of advice in regard to protecting yourself from all this malware we’ve just mentioned, it would be this - learn how not to get phished! This is the most common way that devices are infected with many types of malware.
Both individuals and companies should educate themselves on how phishing schemes work so as to avoid getting hooked. More than anything, go slow when reviewing emails. We tend to get in a hurry and just start clicking. That’s what hackers are counting on.
Here’s the best advice we can offer.
Think before you click.
Obtaining Information
It’s all about information when it comes to the various kind of malware attacks. It took criminals a while to figure it out, but there’s money in information. Lots of money. It follows that most malware is invented and deployed in pursuit of all that information sitting out there on the internet.
Most of us are well-versed in the type of information sought: login credentials, social security, and credit card numbers, mailing addresses, birth dates - the list goes on. The methods by which this information is acquired vary from hacking social media accounts to impersonating public figures or well-known organizations to sitting in a wifi cafe and snagging data packets out of thin air.
Let’s take a closer look at these attacks and exactly how they are deployed.
Phishing Attacks
Phishing attacks fall in the category of social engineering and are a popular way to steal private information. The first step is when the attacker poses as a trusted entity and tricks the victim into opening an email, IM, or text message and then clicking on a link inside it.

There are a couple of different types of phishing:
Whale Phishing
Whale phishing is a variation of the basic phishing attack. The variation is simply that it is an attack focused on a larger (corporate) target, with the anticipated reward expected to be larger than phishing the average individual.
You might think that these high-profile, successful targets wouldn’t fall for a phishing attack. Well, you would be wrong. Back in 2015, an employee at Mattel sent $3 million to an alleged new vendor in China. Since the email came from a company executive, it wasn’t questioned.
There was no vendor in China, and the money was stolen.
Successful whale phishing attacks like this keep hacker interest in the practice high. How high? Very. One out of every 99 emails is a phishing attack, and 30% of them are opened. These are pretty good odds for a whale-phishing criminal.
Worse, 25% of this 1% wind up in Office365 inboxes, which indicates current phishing filters are doing a terrible job at filtering out the junk.
Add to that the fact that 42% of workers self-report having taken a dangerous action that could have resulted in a successful attack - clicked on an unknown link, downloaded an unknown file, or failed to follow best practices to prevent whale phishing. While companies, and probably high-level executives themselves, like to think that they are higher-functioning human beings who wouldn’t fall for a whale phish attempt, reality says otherwise. Everyone in a company, including executives, should be required to attend cybersecurity training that focuses on avoiding this kind of attack.
Spear Phishing
Spear phishing differs from garden variety phishing in a few ways. To carry out one of these attacks, the hacker spends time researching a specific individual and uses the information they gather to create an authentic email.
With spear phishing, the attempted swindle is not a numbers game where millions of the same email might be sent. This type of phishing attempt narrows the target to one and seeks to create a masterpiece fake email that will tempt them to do something stupid.
Due to the potential for an exponentially larger payday, spear phishing has become a sophisticated and popular form of attack. For organized, active hacker groups, spear phishing is used in 65% of attacks. In 95% of the cases, the primary goal of the attack was to gather information.
As we’ve already mentioned, spear phishing is aimed at the “big fish” level of the corporate hierarchy. It is used almost exclusively to penetrate large organization networks. In fact, 95% of successful corporate attacks use spear phishing to get inside.
Large organizations have continued to be a very popular spear-phishing target.
- 88% were the target of at least one spear-phishing attack annually
- 28% were targeted between 1-10 times
- 37% received 11-50 attacks
With the spear phishing market rising above $1 billion in the US alone, employees of large businesses are literally under siege. When spear phishing can land as much as $100 million, as was the case when one scammer went after Google and Facebook, the stakes are too high not to take it seriously.
The top three ways to prevent spear phishing are education, education, and education. Familiarize yourself with spear phishing approaches, and don’t fall for them.
Social Engineering
You probably have heard the term “social engineering” thrown around in the context of online security, and for good reason. Successful hackers have learned to play on our human tendencies to respond to manipulation, deception, or influence in order to get us to purposefully or accidentally disclose secure, protected information or allow access to private systems.
If you think you’re not liable to fall for a socially-engineered scheme, you’re probably wrong. This is one of the top techniques used by online criminals to carry out their malicious plans.
Don’t believe us? Social engineering is used at some point in 98% of all attacks. That’s a big number. Even bigger when you realize that there are 75 times more active phishing websites than those infected straight up with malware.
When you realize that 75% of companies were successfully phished to the order of 241,342 incidents in a single year, it becomes obvious that phishing has become the number one cybercrime. What powers phishing? Social engineering, of course!
The bottom line is that it is easier to fool a human being than a highly-fortified computer network. When it comes to all those big data breaches we still see in the headlines periodically, you can rest assured that about 80% of all data infiltration started with a successful bit of social engineering.
When it comes to social engineering, a common tactic is to impersonate someone from a highly recognizable company like Microsoft. An incredible 43% of criminal social engineers choose Bill Gates’ baby to be the face of their attack. DHL comes in second at 18%, while PayPal, LinkedIn, Google, and Chase get plenty of hacker love as well.
When it comes to social engineering, as a human, you are programmed to fall for it unless you train yourself to be on the lookout for a socially engineered attack. The best advice we can think of is to stay up to date on the typical social engineering approaches and be suspicious of everything.
Sorry, that’s the world we live in.
Man-in-the-Middle Attack (MITM)
The best way to think of a MITM attack is as digital eavesdropping. There are three players in this scenario. There’s the victim, the person at the other end of the conversation, and then we have the “man-in-the-middle” who is listening in and trying to gain some advantage by doing so.
A successful MITM attack relies on the victim being unaware that anyone is listening. A common scenario would involve a poorly-secured wifi connection. It could be a public hotspot or even your home network. It’s easy for a scammer to park in the street and scan for nearby unprotected routers. Then the game is on. With the right tools deployed, any data transmitted through your connection can be intercepted and reviewed at the criminal’s leisure.
The best way to avoid a MITM scheme is to visit only secure websites with HTTPS in the URL field. It’s difficult for a hacker to develop a fake certificate because only five companies supply 98% of the security certificate market for websites, and they keep up a pretty tight defense against bad guys.
While governments or large organizations have orchestrated most MITM attacks, it’s not impossible for a skilled, resourceful individual to find success.
- In 2015, a MITM attack made off with the proceeds of a property sale valued at around $300,000.
- An email MITM scheme rerouted a $1 million payment made between Chinese and Israeli businesses.
Your best defense against a MITM attack is to install an anti-virus and keep it up to date. Additionally, never use a wifi network that isn’t password protected, and always look for the “S” part of “HTTPS” when visiting a site. If it isn’t there, get out.
The same advice goes for all kinds of phishing, social engineering, and MITM attacks. With a majority of people and companies not taking even the basic steps to protect themselves, you make yourself much less of a target by taking just a few preventive actions.
- Learn how social engineering works and don’t get taken in.
- Never click a link or download a file unless you know for sure it is legit.
- Always use anti-virus software, and a VPN isn’t a bad idea, either.
- Maintain a defensive mindset.
The basic idea we want to leave this section with is that hackers are going to go after the easy game. Don’t be an easy game; there is a good chance they will leave you alone.
Server / Server-Client Attacks
We’ve mentioned a few times the typical hacker’s thirst for information. That’s why they do what they do. Knowing this, it’s no surprise that cybercriminals often mount attacks on servers because that’s where the information is.
These web servers are the brains and engines of a website. Here’s the short version of how it works. Your operating system hosts apps that connect to a server database. The app reaches out to the server and receives the files that make up a web page in return to display for you.
A web server is typically a high-value target precisely because of that information and is more liable to be well-protected. Breaking and entering servers is a complex bit of hacking that not all online criminals are up to.
Check out some of their favorite tactics below.
Distributed Denial of Service (DDoS) and (DoS)
Both of these types of attacks take the form of bombarding a server with requests until it is overwhelmed and cannot respond to legitimate queries. Typical targets for a DDoS or DoS attack are governments or large credit card companies.
The end goal is to make a target website unusable by overloading it to the point that it crashes.
Hackers who choose to roll out a DDoS or DoS attack are sometimes bent on blackmail, sometimes on simple mischief, and other times involving themselves in politics. One thing is certain. This attack vector is popular and getting more so every year.

For example, there were 7.9 million recorded DDoS incidents in 2018. That number is expected to grow to 15 million by the end of 2022. This is despite an FBI campaign to close down large-scale operators. There have been 15 such operations shut down, but more have risen to take their place.
File this in the drawer of obvious statements, but DDoS attacks occupy a lot of bandwidth. When an attack like this is underway, as much as 25% of a country’s total internet traffic is liable to be devoted to an underway incident. A single server assault can take up as much as 587 GB.
Have you heard of the Internet of Things (IoT)? In short, it is a subset of the overall internet and is made up of all those little smart things that connect to the internet - security systems, smart appliances, and fitness trackers. They need a live internet connection to work.
DDoS and DoS criminals love the IoT. Why? IoT devices are some of the least secure online components to be found. It’s easy to get into these types of networks and turn them into bots to deploy in the attack. There are already more than 20 billion IoT devices in use. Expect that number to increase exponentially in the foreseeable future.
Thanks to the IoT, the popularity of DDoS will probably continue its healthy growth.
Which countries catch the majority of DDoS and DoS attacks? The unfortunate leader is China at 63.8% and the US at 17.5%. After that, it drops off quickly, with Hong Kong coming in third with 4.61% of attacks.
Coincidentally, China and the US are also the most popular originators of DDoS attacks. China exported incidents 4.5 million times and the US 2.7 million over the course of a year.
We have already seen a handful of historically powerful DDoS attacks this year. While the cybersecurity experts who helped to mitigate the onslaught are reluctant to name targets, it was a company in the financial industry. At one point, their servers were being buried with 17.2 million requests per second. Botnets are alive and well in 2022.
SQL Injection
SQL injections have been responsible for hacks of some of the biggest companies out there - Target, Yahoo, LinkedIn, and Sony, to name a few. Cybersecurity experts tell us that SQL injection is one of the easiest hacks to defend against. Obviously, some of the world’s finest operations are not taking the threat seriously.
In simple terms, an SQL injection hack occurs when a criminal writes malicious code into common web forms like a search, login box, or even the URL field. Once into the system, it’s simple to steal, delete, modify data or even take over administrative control of any device in the network running the infected application.
Before we jump in deeper, you probably want to know what (structured query language) SQL is anyway? Developed in the early 1970s, it is one of the oldest programming languages used to manage databases.
The first SQL injection was documented in 1998. Writing under the pseudonym Rain Forest Puppy, a hacker described how someone with basic coding skills could load unauthorized commands onto legitimate commands and find themselves in the database of an unsecured site.
By 2007, hackers were beginning to take this process seriously. Russian hackers exploited the 7-11 websites, specifically the customer credit card database. They began withdrawing cash, eventually to the tune of $2 million.
Some SQL attacks aren’t money driven. During that same year, hackers SQL injected their way into a couple of US Army websites and directed visitors to various other sites dedicated to anti-American and anti-Israeli propaganda.
A year later, MySpace (remember that social media dinosaur?) lost emails, names, and passwords to almost 360 million accounts.
We’d like to stop there because you probably get the idea, but there’s one more example we can’t ignore. You’ve heard of Equifax, right? One of the big three consumer credit agencies? Back in 2017, this protector of our most sensitive information somehow fell victim to an SQL attack that yielded names, social security numbers, birth dates, and addresses for 143 million customers.
Ouch. Talk about scrambling to explain a fiasco.
As recently as 2017, the Open Web Application Security Project named SQL injection as number one on their list of Top 10 Most Critical Web Application Security Risks.
Statistics show us that as many as 25% of all businesses have at least one SQL injection attack in a year. While this threat vector has neither been improved nor changed, it is significant enough to pay attention to.
So if the question is, “Are SQL injections still a thing?”, the answer is a solid “Yes” based on the 1,162 vulnerabilities that can be blamed on this attack vector so far in 2022.
Cross-site Scripting (XSS) Attacks
Cross-scripting attacks are a form of injection but differ from SQL injection in a few critical ways. With XSS, the malicious code is injected into an otherwise trusted site through a browser-side script to a random end user.
Because the browser thinks the script is safe, it executes it. At that point, the hacker can access cookies, session tokens, or any other information retained by the browser while on a particular site.
While not the leader of the hacking world’s attack vectors, cross-site scripting is used often enough to pay attention to. Research has shown that around 60% of all web applications are vulnerable to an XSS attack and 30% of attacks are of the XSS variety.
In actual numbers, XSS injections have grown over the past decade from a mere 470 in 2011 to 22,000 in the first four months of 2022. According to the security company OWASP, the severity of XSS attacks has scored 7.25 out of 10.
Gain from OWASP - the frequency of XSS in the wild coincided with the change over from HTML to XML website coding language.
A recent successful XSS injection occurred in the popular multiplayer online game Fortnite. With over 200 million users, this was a worthy target for hackers. The vulnerability was inadvertently created when an obsolete web page was retired. The problem was that they never took it down. It was only a matter of time before a hacker found it.
Once inside the Fortnite site, they had access to all the players’ data. Luckily, the vulnerability was discovered and fixed. While no damage was ever detected, the potential was there to steal game currency and record conversations between players, which would have created a serious advantage for the hacker if they were a Fortnite player also.
DNS Tunneling
DNS tunneling is a damaging attack vector that gets a lot of publicity in the computer nerd community but not much from the cybersecurity press at large. Why is this? Likely because it’s not easily explainable in layman’s terms.
We’ll give it a shot anyway.
Are you familiar with the term DNS? This stands for domain name system and is the protocol used to make human-friendly URLs like www.MyCoolWebsite.com readable to machines and vice versa.
Since DNS is not used for data transfer, its traffic is not usually monitored, which is great news for skilled hackers. Long story short, a DNS tunneling attack is engineered by a hacker buying a domain name and pointing nameservers to it. They install tunneling malware on the site. With this setup in place, all that’s left is to infect a computer behind a firewall. Since DNS requests are allowed free passage through a firewall, it’s an easy enough matter to set up a tunnel between the infected computer and the website with the tunneling malware.
At this point, the hacker can waltz in and take whatever data they want at their convenience. It’s difficult to trace a DNS tunneling attack because there is no direct connection between the attacker and the victim.
As mentioned, DNS tunneling attacks can be a financial drag to a business.
- 79% of companies experience at least one DNS attack per year
- Average damage is $924,000, including downtime costs and cleanup
- 77% of companies see DNS security as critical
What does this tell us? Companies are starting to take their DNS security more seriously. Notice we said starting. It’s not a full-blown thing yet.
- 25% of companies perform no analytics on their DNS traffic
- 35% don’t filter their internal DNS traffic
- Only 12% collect DNS logs
Meanwhile, DNS data theft is up 10%. Some experts attribute this to the fact that firewalls have never been that good at detecting DNS attacks and are even worse at keeping them from infiltrating a network and making off with data.
Recent DNS tunneling attacks have been deployed to take advantage of the Covid-19 pandemic through NRDs (newly-registered domains), defined as any registered within the last 33 days.
A DNS tunneling attack is launched by opening a domain that varies slightly from the legitimate one. With pandemic-inspired attacks, a hacker would simply go where the interest was online. In the early days, people were searching for Covid news and test kits in large numbers, so hackers would pose as government agencies offering free money or information.
Two years into Covid searches for vaccine information have picked up and so have illegitimate sites intended to dupe users into providing their private info. With DNS-based malicious operations, cybercriminals typically shut down a fraudulent website quickly, making it hard to trace.
DNS Spoofing
DNS spoofing is sometimes referred to as DNS cache poisoning. This type of hack involves the bad guy or gal injecting bad data into a DNS resolver cache. This results in the nameserver sending back a bad IP address, which allows traffic to be diverted to another site that is controlled by the bad actor where, once again, they will try to trick visitors out of their personal data.
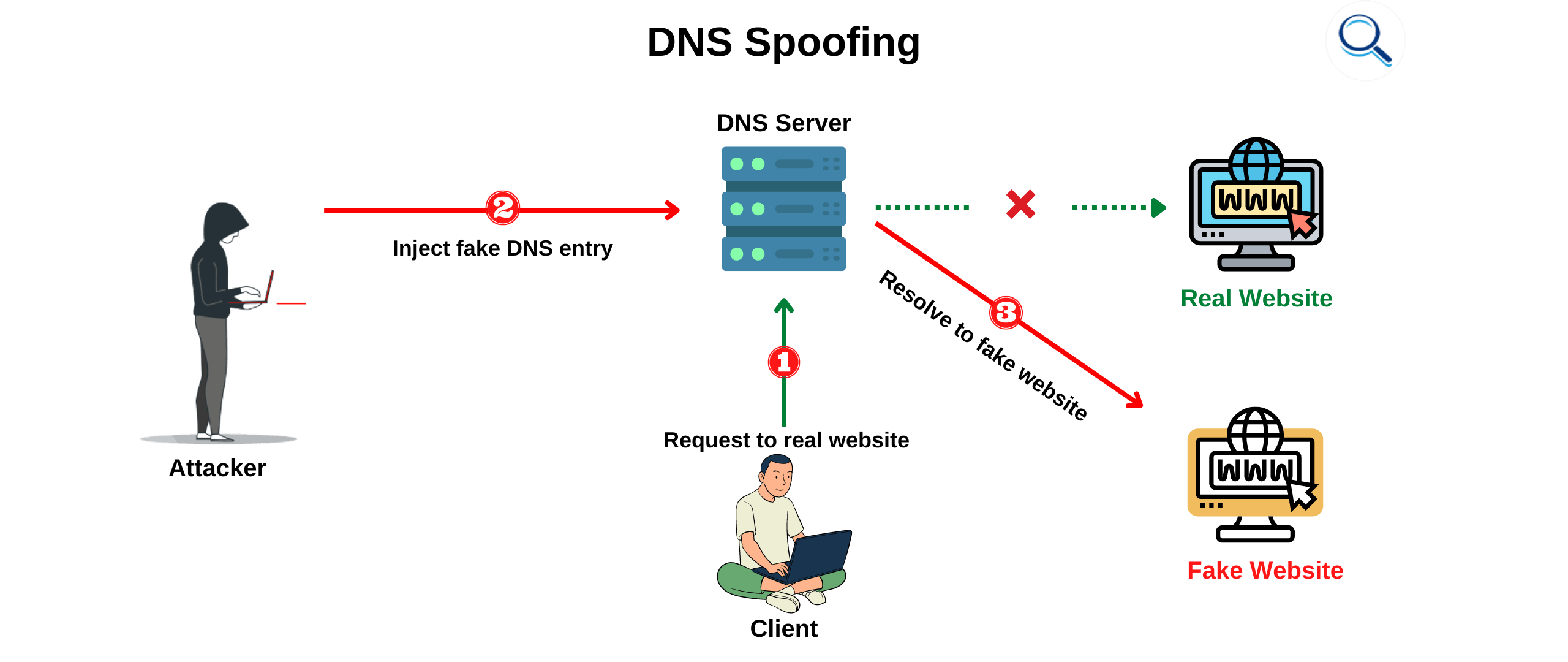
DNS spoofing is also an excellent way to censor what people see online. The Chinese government has deployed this form of information control for years.
These kinds of spoofing attacks have been on the rise, along with most other forms of online threats. One report surveyed business owners and found a 125% increase in the number of incidents that rerouted traffic to a fake site.
As the internet has moved to the cloud and remote work has become the norm, it’s natural that we would see a rise in misconfiguration attacks there as well, which we have to the tune of a 77% increase.
Before the Covid-19 pandemic, not many employers paid attention to DNS-based intrusions. That has changed considerably, with 55% now citing DNS security as critical in relation to a permanent remote workforce. A full 51% are looking at setting up a DoH (DNS over HTTPS) to keep company communication safe.
Add to this the 75% of company respondents who say they are looking into creating a Zero-Trust Initiative, and you realize how aware organizations are about DNS attacks these days. You don’t have to understand Zero Trust or DoH other than to know they are defensive measures targeted to avoid DNS spoofing and other similar attacks.
What happens to those redirected to a fake site by a DNS spoof? That varies, but it’s rarely a good thing.
- 70% received malicious browser ads
- 51% encountered ransomware
While DNS spoofing has never been the most common threat vector it remains a viable tool in a hacker’s malicious kit due to the skills needed to carry it out successfully. From the hacker’s point of view, DNS spoofing can be executed by a variety of methods that all rely on glaring deficiencies in DNS security. To the end user, pay attention if you start ending up on sites you never intended to. There might be a spoofer at work.
URL Interpretation
This benign-sounding cyber attack can create all kinds of chaos in your online life if it is successful. Instead of going after the weak security of a site’s DNS, hackers target the Uniform Resource Locator (URL), which is the field at the top of a browser where you type in the page you want to visit.
Also called URL poisoning, in this kind of attack, hackers take advantage of yet another security-deficient part of the system to wreak havoc. Criminals can manipulate an URL by using software to enter different values based on an educated guess and the fact that a website’s naming convention often follows a predictable pattern. While there might be no link available to go to an unpublished or secret page or even a database, you can often get there any way through URL interpretation.
Another tactic deployed through this kind of attack is to record a user’s browsing pattern by figuring out and tacking a session ID number onto the URL. A hacker can then follow along as a user navigates from site to site.
The real danger comes in when the oblivious user logs into banking sites or other places where they access sensitive information.
As basically a trial-and-error approach to hacking, URL interpretation is not the most popular choice for criminals to achieve their wildest dreams of illicit wealth. Still, website owners would be advised not to leave any of their pages with easily guessed names.
Session Hijacking
Sometimes called cookie hijacking, session hijacking refers to the idea of a hacker tricking the computer browser or web app into thinking it’s you when it isn’t. Session means your internet session. Say you’re heading over to Bob’s Country Wear to buy a new outfit for next week’s square-dancing competition.
If your session gets hijacked, the hacker can do anything you could do, including spend your money, and change your shipping details. You get the idea.
In comparison to some of the hacking methods we’ve recently mentioned, session hijacking falls somewhere in the middle of the pack when it comes to popularity. Still, a recent report found that 31% of eCommerce applications are at risk.
Think of how many sites or accounts you log into daily. A bunch, right? Imagine a hacker being able to penetrate each and everyone just by stealing cookies and following you around.
Today’s “connected” lifestyle puts almost every aspect of our life at risk, which keeps the bad actors returning for more.
Session hijacking is based on a simple concept. When you log into a web application - let’s say you do your banking online - the server you’re accessing leaves a temporary session cookie in your browser. This is how the remote server keeps track that you have been authenticated and are logged into the app.
The hacker needs to know that session cookie ID in order to consummate the attack. There are a handful of different ways, but it usually involves tricking you into reading a phishing email and clicking on a malicious link.
One technique is called session sniffing. Here’s how it works.
For success, a hacker has to monitor unprotected traffic in order to read what the session ID is. After that, it’s easy pickings. It should be obvious that the way to prevent this particular attack is to prevent the hacker from being able to see your traffic.
Good job! You’ve been paying attention. That’s why encrypting your internet session through a VPN makes so much sense. At less than ten bucks per month, it’s a marvelous way to prevent session hijacking.
We’ve touched on some of the popular attacks in this section, but there are many more - too many to go into depth about and warn you specifically about how to protect yourself. If you’re concerned about getting hacked - and you should be - there are a few basic steps to take that offer protection from most attacks. Here are our top five.
- Use an anti-virus with malware protection as well as a VPN
- Update security software regularly
- Learn about phishing, and don’t fall for it
- Watch for the HTTPS (especially the “S”) in the URL of any site you visit
- Enable two-factor authentication where available
Will doing these things protect you absolutely? Absolutely not, but it will make you a more difficult target than most people, and hackers love picking the unprotected low-hanging fruit.
Password Decryption
You’ve probably noticed that the online world revolves around passwords. If you’re like the average surfer, you need to enter a password to access a product, service, or site dozens of times a day.
Count ‘em up if you don’t believe it. You might have to use your toes. The serious point is that if a bad actor breaks a password, you’re in deep doo doo, especially if you’re one of the seventy kajillion people who recycle the same password over many or all of their accounts.
As a side note, this is a very bad idea which we will talk more about later.
So, how do hackers break passwords? Here are the most popular ways.
Brute Force
A brute force attack is just what it sounds like. A hacker sits there at your account and tries different passwords until they stumble across the right one. With the millions and billions of combinations available with even a simple password, you might feel all warm and snuggly safe.
The bad news is they aren’t doing this manually. It’s easy to use a bit of software that automatically sifts through password variations while the hacker sits back with a sweet tea and listens to Jimmy Buffett. All they have to do is push a button and let it work away at busting your account wide open.

With brute force attack software cheap and widely available, it’s no surprise that attacks have increased, especially since the pandemic.
Kaspersky counted the number of attacks in the US at around 200,000 before the pandemic. Apparently, with all that extra free time gained through lockdown orders, hackers did more than just twiddle their thumbs. Early in the pandemic, brute force attacks jumped to 800,000 and then soared to 1.4 million as time went on.
We’ll leave you with this. A Verizon report revealed that 80% of breaches caused by hacking can be attributed to brute force attacks and the use of lost or stolen credentials. With so many more people working remotely, hackers may have also discovered that breaking into systems outside the protection of corporate IT department watchdogs is easier.
Dictionary Attack
This type of password-breaking might not use a literal dictionary, but it could. The term “dictionary attack” refers to a hacker systematically trying entries from lists of common passwords to break into a target’s account.
They might try popular pet names, fictional characters, or the aforementioned dictionary. They also check common variations like “p@ssw0rd.”
As with brute force attacks, expect a dictionary attack to be automated so that a bad actor can make thousands of attempts in a short time.
Hackers often prefer to run a dictionary attack than a brute force attack because it is more likely to be successful. Think of it like this. There are around 1,022,000 words in the English language. Add in the numbers 0-9, and you have 218,340,105,584,896 possible combinations if you are using an eight-character password.
Where brute force relies on the hacker’s computing power, a dictionary attack is more targeted and likely to hit on the right combination sooner.
While a dictionary attack is a form of brute force, it’s more efficient because it is based on human nature when it comes to choosing a password.
When it comes to choosing a password, length isn’t necessarily the determining factor for how strong it is. A computer takes the same amount of time to check the word “pachycephalosaurus” as it does to check “cat.” The trick is to be unpredictable. Make up new words. Throw in special characters or strings of nonsense. This kind of thinking is what keeps your password off the dictionary attack lists.
And lest we think that breaking passwords is a technique of the past, we’re here to tell you it remains quite lucrative.
Ask the folks over at T-Mobile, who lost $350 million in a recent breach. Or the Los Angeles Unified School District that had 500GB of private information divulged publicly when they refused to pay a group of Russian hackers after a successful ransomware attack. ‘Nuff said.
Keyloggers or Keylogging
Keylogging differs from brute force and dictionary attacks in that it uses malicious software to record the keystrokes you make. Once a hacker has that information in hand, it’s simple to go back through the data and reconstruct the password you have used to access a particular account.
Keylogging is a level of sophistication up from the others we’ve discussed but has little chance of success without the hacker being able to gain the unwitting assistance of the victim because they first have to gain access to the target’s computer to install the keylogging software.
For this, they typically turn to phishing. As we’ve mentioned before, around 80% of breaches rely on the human element to get the ball rolling, and keylogging is no different.
The originators of keylogging were Russian intelligence agencies back in the 1970s. Since then, it has evolved into the sixth most popular form of enterprise malware. The interesting thing to note is that keylogging has some legitimate uses.
- Parental supervision of a child’s browsing habits
- IT assistance and troubleshooting
- Approved device monitoring
- PI work in adultery or other cases
Keylogging software is a form of a virus and typically is sideloaded as part of a Trojan suite that might include adware, spyware, ransomware - really, anything the hacker feels like throwing at you.
As a virus, keylogging can spread. With the percentage of organizations that have had viruses spread from one machine to another hitting 75%, this is no small deal. What starts as a simple penetration of one machine rapidly becomes a company-wide crisis.
Are you ready for something even scarier? Of course, you are. Some sophisticated keylogging attacks don’t even rely on installing software on the victim’s device but can analyze the specific electromagnetic traces emitted by a keyboard up to 66 feet away. Suddenly that cozy spot and public wifi down at the local coffee house don’t seem quite so appealing.
Vulnerabilities and Exploits
Bad actors love exploits because it makes their hacking job so much easier. An exploit is nothing more than a poorly-coded section of legitimate software that creates a back door through which hackers can shove malware into your system.
Microsoft Word is a good example. Older versions of this flagship product still carry coding errors which can be leveraged through malware installation to allow access to privileged information. Why go through the front door and go toe-to-toe in a battle against Microsoft’s stalwart anti-malware software Microsoft Defender when you can sidestep your way through Word and never have to land a punch?
The number of reported exploits (also referred to as vulnerabilities) is mind-boggling. The US government maintains a database of these bugs with 176,000 entries. This offers enterprising hackers a world of possibilities to ply their malicious trade.
The first quarter of 2022 brought us 8,000 additional exploits, a 25% increase from the previous year. One vulnerability report says that 10% of all web applications contain either a high-risk or critical problem with code that could be exploited. This number rises to 15% if the app is a payment processor.
Exploits seem to be a problem of size. In other words, larger companies with more than 100 employees have a much higher incidence of high-risk or critical problems.
But a company quickly fixes a vulnerability once it is discovered, right? If only! The same report estimated the time it took to fix this sort of problem (Mean Time to Remediation or MTTR) is 58 days. A dedicated hacker and all their hacking friends can do a lot of damage in two months.
But that 58 days is the median. There are outliers like the CVE-1999-0517 vulnerability that has been live for 23 years. This exploit allows access to a device on a network that scores a 7.5 / 10 and makes it a high-severity problem.
Since 2020, vulnerabilities have been appearing in major cloud infrastructures, the first example being Microsoft Azure. An article detailing the problems was released for the purpose of showing that moving to the cloud wasn’t a panacea of impenetrable security. The vulnerabilities were scored 10.0 / 10.0.
Obviously, most companies want to close an exploit as soon as it is discovered. A recent example of slow response was the Follina exploit, which appeared in April of 2022 and allowed successful hackers to execute malicious PowerShell commands through the Microsoft Diagnostic Tool.
In late May, Microsoft finally got around to issuing recommendations that described how to workaround the exploit and mitigate against any malware that had already been introduced.
When an exploit is first discovered by hackers, it is referred to as a zero-day exploit. Word spreads fast on the Dark Web telegraph, and bad actors rush to take advantage before the hole closes.
The interesting thing to note about zero-day exploits is that they seem to fluctuate. There were 36 tracked in 2020 and 83 in 2021 but only 18 in the first of 2022.
Statistics on Cybersecurity Attack Targets
Bet you thought we’d run off and forget about the second part of the Cybersecurity Trifecta. Nope. Here it is. The following section digs into the numbers behind the unfortunate victims of the hacking industry, and there are plenty.
From the lonely senior citizen hunting and pecking her way through a YouTube quilting video to the largest corporations on earth, no one is immune from these attacks, and sometimes the damage can be substantial. Let’s start with the biggies.
Large Corporations
While one would presume that massive companies would pour enough resources into defending their networks that they would never suffer a breach, the key idea here is that they probably do. The problem, as we’ve mentioned numerous times already, is the human element.
At any point in time, there are disgruntled, tired, or gullible employees. Each one represents a chance for a phishing attempt to succeed, and a lot of times, they do. Let’s break this down by industry.
Healthcare
Hospitals, clinics, and pharmacies represent an enticing target for a hacker bent on mischief or profit. Perhaps more than any other industry, healthcare is a treasure trove of privileged data flying around through a maze of imperfectly connected systems.
Attack vectors are everywhere, and criminal thinking says that a hospital would have a hard time bargaining against ransomware with human lives at stake.

Impact of Cyber Attacks
Attacks on healthcare organizations have been on the rise, which is an impact in itself, but the life-and-death scenario we mentioned is the wild card. Consider ransomware loose in a patient record database, and the records get locked down or encrypted - unusable.
Without access to patients' updated charts and meds, it doesn’t take much imagination to see where that leads.
2021 was a “banner year” for patient data theft. 40 million records were compromised in the US alone. That total was accomplished through 905 individual attacks and reflected a 44% rise in healthcare hacks from the previous year.
Of that 40 million, more than half - 22.6 million - were patient records, some of the most sensitive data healthcare organizations handle.
Remember a few paragraphs back when we mentioned ransomware? It wasn’t just because we like to say the word. It’s becoming a big deal in healthcare. Of all the ransomware attacks launched in 2020, 60% were aimed directly at healthcare.
Healthcare hacking is turning out to be a small and medium-sized hospital problem. For these organizations, 48% of CEOs report having to shut down to some extent at least once in the past six months.
The costs associated with shutdowns (the average length of time is six hours) are staggering. Large hospitals report a cost of $21,500 per hour. This is bad enough, but you can more than double that number when it comes to smaller hospitals - to $47,500. No organization can absorb these kinds of financial hits forever.
There’s something we haven’t mentioned yet about why smaller hospitals are being targeted. Typically, a smaller size is associated with a smaller cybersecurity budget, leaving an easier path for hackers to find their way in. In the past, they may have been able to get away with not making cybersecurity a top priority.
Those days are likely gone.
Cybersecurity Initiatives
So, what is a hardworking healthcare organization to do in the face of this all-out assault on its security? Sit back and take it? Nope. Though the numbers we’ve just thrown out indicate that hackers show no signs of letting up, the good guys have a few tricks up their sleeves as well.
The latest network paradigm for healthcare organizations has been to pull back somewhat from the full-on cloud computing model and adopt a hybrid model called edge computing. Some are finding out the hard way that this change necessitates a cybersecurity thought shift as well.
Despite a series of high-profile breaches dating all the way back to 2011 and each costing millions, it seems hospitals have only begun to get serious about cybersecurity recently. To date, spending on cybersecurity has been bafflingly small, with healthcare coming in 9th in security spending to other industries.
The tricky part in deciding what to spend money on - as healthcare struggles to play catch up - is identifying where they will get the most bang for the buck. Current initiatives and recommendations from cybersecurity companies have suggested they focus on the following.
Device Security: Medical passwords should be updated often and not re-used across different systems. They shouldn’t be left on when not in use. Any IoT devices with weak inherent security need to be monitored frequently and strengthened or replaced when possible.
While the real-time tracking capability of the IoT makes the technology almost indispensable, its security has to be hardened. Medical spending on the IoT is expected to reach $137 billion in 2021, and a global presence in 60% of global healthcare facilities. Ransomware will continue to be a popular threat vector. Internal servers should be secured against it.
Early Risk Identification: Don’t wait for ransomware or other malware to show signs of having made it into a system. Go out and look for it regularly. This means a proactive program of scans and expecting attacks to increase on weekends and holidays. Much of this can and should be automated. Fully automated risk detection initiatives have been shown to save $3.58 million ahead of companies that don’t.
Backup and Update: This part of the cybersecurity equation sounds boring, but it’s critical. The best defense against a ransomware attack is having your entire system regularly backed up to secure servers. When ransomware attacks like WannaCry can hit more than 15 countries, the best defense is to be able to purge your system of the corrupted data and install a clean copy.
Otherwise, be prepared to pay a ransom demand like the hospital that decided to cough up $55,000 to get their data back from yet another ransomware known as SamSam.
Constant Education: Constant education is a hassle. Ultimately, though, there is no better way to thwart cyber attacks that to have a knowledgeable and engaged workforce who are a critical part of the cybersecurity fight. They are the ones with hands on the data and devices and need to be the ones who can recognize an attack early on and notify IT to shut it down. Hiring a cybersecurity pro to deliver frequent classes is now a must.
Notable Cyber Attack Incidents in 2022
Attacks on healthcare systems have been a part of the post-pandemic landscape. Here are two to be aware of that have happened this year.
The Yuma Regional Medical Center in Arizona was the victim of a ransomware attack in April 2022. Protected medical information for 737,448 former and current patients ended up being compromised. Neither the medical center nor the police released information related to a specific ransom demand.
The breach went undiscovered for four days, a time during which some records were taken out of the system. Operations were slowed for a short time while a backup copy of all data was installed. Officials for the medical center said cybersecurity would be enhanced immediately.
The Baptist Medical Center in Texas was breached by an unauthorized third party, resulting in malware being placed into their system that affected more than 1.2 million records. The theft was ongoing for almost a month (from March 31 to April 24). A national cyber forensic team was brought in to immediately close the breach and assist in the remediation
With 17 major breaches documented by the HIPAA Journal in the first half of 2022, the industry still has some work to do.
Energy
Attacks on the energy industry and its infrastructure have the potential to be a national disaster. Disruptions to the flow of oil and gas on a large enough scale could bring our transportation system to a stop. You don’t want to follow this line of thinking too far but at least consider this nightmare scenario:
- A breach shuts down large sections of our oil refineries
- No oil is available to be converted into gas
- Trucks have no fuel to deliver groceries to stores
- Shelves are empty
- Chaos ensues
While supply chain issues appeared during the pandemic on a small scale, it could have been worse - MUCH worse - had a computer attack shut down critical systems en masse and for a long period of time.

Impact of Cyber Attacks
While data breach information for 2022 is still being collected, the energy sector has experienced a measurable impact from cyber attacks in recent years. For example, 2021 had 976 successful breaches that affected 20 companies. This was down a little bit from the previous year but still of concern.
Overall, 1,504,564 records have been exposed and/or stolen since 2018.
The types of records that were exfiltrated were primarily email/password combinations and banking/financial records.
Fortunately, there were few instances comparable to the Colonial pipeline shutdown, which we’ll discuss in more detail in a moment. The main lesson from these breaches is to illuminate the reality of how vulnerable the industry’s systems are. The next major malicious shutdown could be right around the corner.
Cybersecurity Initiatives
While cyber-attacks have been on the rise in a number of industries - we just discussed healthcare problems in this area - there’s not much use in identifying problems unless there is a well-thought-out plan to address and improve the situation.
The scope of the problem is obvious, especially in the US, which suffers 31% of global attacks, most of which are aimed at (and often successful) targeting top-level energy CEOs. India comes in second at 4%. An industry researcher found that 25 of the top 55 executives questioned had been breached at some point in the past four years.
Much of the cybersecurity progress to be made is contingent on the changing whims of different presidential administrations and congressional turnover, as well as the tortoise slow process of creating (or removing) federal rules and perpetually inefficient communication between the federal government, especially the intelligence communities) and private energy sector leaders.
Perhaps the critical nature of communication is no better seen than in the fact that 80% of critical energy structure is owned by private entities, but it’s the government’s job to protect it.
But there has been some forward movement.
Three programs intended to improve energy sector cybersecurity are worth mentioning.
Cyber Testing for Resilient Industrial Control Systems is pushing the idea of proactivity. Specifically, this program aims to create a system of scanning software and firmware on a regular basis and address threats sooner rather than later in order to avoid disruptions in the supply chain.
The second big industry push is to move beyond the current patterns of patching old systems, paying off hackers, crossing fingers, and just accepting breaches as part of the business. The new thinking is to create a cybersecurity process that is baked into the IT system from the beginning.
The last big program repeats a theme you’ve seen in this article before. Education! The energy industry needs a workforce educated in basic cybersecurity priorities, concerns, and best practices. Informed workers will be able to go beyond the “patch it and pray” mentality and create modern networks able to withstand the onslaught of today’s sophisticated hackers.
Notable Cyber Attacks in 2022
In 2022, there has been one major breach and several smaller ones. Here’s what we know about them so far.
The big one was the Colonial Pipeline which provides 45% of the east coast’s fuel. A breached password (suspected to have been found on the Dark Web) was all it took to set off the biggest energy industry security incident of 2022.
The Colonial Pipeline, located in the northeastern US, was penetrated through a VPN account. After the breach was discovered, Colonial officials decided to shut down operations and freeze IT systems. The bottom line was that the perpetrator turned out to be ransomware supplied by the well-known hacker group DarkSide.
Colonial eventually paid a $5 million ransom and was able to return to normal shortly thereafter.
A second 2022 incident that made headlines occurred in the Florida city of Oldsmar when a hacker was able to infiltrate the drinking water treatment systems and introduce chemicals up to a deadly range. The attacks occurred on February 5 when a hacker broke into a computer system set aside for remote control of treatment operations.
The first incident was only for a few seconds. The next one lasted five minutes before a sharp-eyed employee noticed a cursor moving by itself on the screen. The hacker upped the level of lye from 100 parts per million to 11,100 parts per million.
The change was shut down before any tainted water found its way to the general public. Particular remediation steps have not been disclosed, but it seems like whatever defensive processes they have in place worked this time.
Finance
The finance industry is another that finds itself in cyber criminals' crosshairs (obviously) because that’s where the money is. Banking sector cyber attacks rose in the wake of the pandemic by 238% in 2020 as compared to the previous year. When a typical data breach costs $5.72 million to recover from and remediate, you can bet companies are paying attention.
How much? Let’s take a deeper dive.
Impact of Cyber Attacks
The impact of attacks on financial institutions goes deeper than a simple loss of money. It degrades public trust and permanently damages a company’s reputation. If any industry needs to figure out how to become more resilient to cyber criminals, it’s finance.
The numbers themselves are pretty big.
In the first half of 2021, ransomware attacks on financial institutions increased by a staggering 1,318% year-on-year. By the year's second half, the industry was receiving 22% of all ransomware targets. Costs occur in the ways we’ve mentioned, plus a few more.
- Customer compensation
- Share price drops
- Reputation damage
- Civil or criminal lawsuits
A 12-month study by IBM of 550 industry organizations found that only healthcare was targeted more often and had to spend more money to recover.
Cybersecurity Initiatives
Regulatory requirements and the desperate desire to protect their brand are the primary drivers behind the cybersecurity push in the finance industry. Hackers focus on bank-held information only slightly less than healthcare information, and high-value items like home addresses, social security numbers, banking account info, phone numbers, email addresses, and even income information are the targets.
These kinds of records in bulk bring a pretty penny on the Dark Web.
As an industry valued at more than $22 trillion, it has a vested interest in figuring out how to stop hackers. The current thought in finance is to focus on response, resiliency, and resources.
A big problem is that institutions still rely to a large extent on legacy systems that would be prohibitively costly to replace, so they patch it up and keep limping along. Many banks have still not implemented such simple but effective processes as requiring 2FA for customers logging into their accounts.
Multi-factor authentication, or MFA, means a hacker must have physical possession of a target’s computer and phone simultaneously to access the account. This raises the difficulty level considerably. Cybersecurity experts urge finance leaders to invest in technology and workforce education.
The unquestioned weakest link in finance cybersecurity is the human element and the ever-present threat of social engineering. Social media platforms are popular spots for hackers to meet and groom potential targets for future evil-doing.
The stark reality is that regulatory requirements and the costs of creating a resilient, compliant system might be too much for some banks to bear. We might see a shaking out where only the strong survive over the next few years.
Notable Cyber Attacks in 2022
There was no shortage of financial institution penetrations in 2022. Here are a couple that is noteworthy for different reasons.
Flagstar Bank Data Breach: This one occurred in June and affected 1.5 million customers. The interesting part was that no information was stolen or used maliciously in any way that the company could find. Talk about catching a break.
You can bet that the IT department is checking their shorts for stains and counting their lucky stars. Hopefully, they are also looking into what went wrong to ensure it doesn’t happen again.
CashApp Data Breach: This one actually happened back in December of 2021, but the company didn’t get around to reporting it until April 2022. Understandable since it affected 8.2 million customers. News of the problem didn’t come to light until a Security and Exchange Commission report revealed the details.
It turns out this breach was an inside job in which a former employee downloaded customer data. Apparently, no critical information was affected. Law enforcement was notified, and an official investigation is underway. A forensics firm was hired to look into the technical side of the breach and make recommendations to the company on how to prevent future similar occurrences.
Education
While the education sector isn’t seeing as many breaches as the healthcare and finance industries, and it typically isn’t life or death or financial ruin when there is one, that doesn’t mean people don’t get hurt when their education is disrupted.
With around 57 million students and another close to 4 million teachers heading off to schools this fall, that leaves a big potential audience with which for hackers to ply their naughty trade. In recent years, schools have proven to be a popular target for ransomware.
Impact of Cyber Attacks
While education ranks the lowest of the five industries tracked by the Identity Theft Resource Center, there still were a worrisome number of recent breaches.
- 2017 - 128 breaches
- 2018 - 76 breaches
- 2019 - 104 breaches
- 2020 - 1,825 breaches
That 2020 number caught the attention of cybersecurity experts and accounted for about 13% of all breaches. Of successful education breaches, 52% were ransomware. The major impact is felt as a result of canceled classes, inaccessible online learning platforms, and the danger of falling behind in educational goals.
And that doesn’t even consider the millions of private records and data exposed over the last several years. Damage on that front is hard to access because it might be years before it shows up for sale on the Dark Web and turns into an actual identity theft problem.

Cybersecurity Initiatives
Cybersecurity experts are in the process of introducing new strategies to the educational environment that should make it more difficult for hackers to break in.
The first is to realize that education is a target. Some would call it a soft target because many schools are behind the curve when it comes to realizing that the data they hold is valuable to malicious actors.
Think about the data maintained in any school or university’s network: birth dates, social security numbers, addresses, bank account info, and even credit card data. This lack of awareness manifests in small or non-existent cybersecurity budgets. This has to change and is in the process of doing so.
Put that newfound cybersecurity awareness into action by including it in the curriculum for administrators, teachers, and even students. Younger students should be introduced to the concept of cybersecurity and the basic things they can do to be safe and keep their school safe online.
College-aged students in some institutions are required to complete a cybersecurity certificate course before being allowed into their school’s networks. The big issue here is to understand what social engineering is and how to not fall for the tricksters who use it.
Following up on the idea of social engineering. It’s important enough to deserve its own section. Perhaps more importantly than any other single action, a school district or university can take is to train all employees, students, educators, and administrators on the fine art of repelling social engineering attacks.
Schools are in frequent contact with parents and students who request information. Hackers love to insinuate themselves into the pipeline. Educators need to know the common methods they use and train themselves not to fall for them.
When all else fails, try money. It can be hard to get the buy-in needed to implement a fully-functioning cybersecurity education. It’s not that people don’t want to contribute to the organization’s safety. It’s just easy to get busy and forget to be proactive. If other tactics aren’t gaining traction, try cash rewards for identifying vulnerabilities, security risks, or attempted hack attempts.
Notable Cyber Attack Incidents in 2022
Choosing from the hundreds of education breaches in 2022 wasn’t difficult. A couple of large ones from either coast stand out.
New York City Public Schools: This one is likely the largest reported educational breach in US history. When the dust settled, more than 820,000 current and former students had their private personal and financial data compromised. This included names, birthdays, ethnicities, free lunch, and disability status.
The break-in was traced to specific third-party products which had neglected to encrypt data, leaving hackers an easy path into the system. Remediation efforts have focused on deleting data from third-party use once it is no longer needed and ensuring third-party relationships are entered only with vendors who encrypt data.
Los Angeles Unified School District (LAUSD): On the other side of the country, the LAUSD found its computer network hacked by ransomware deposited by an online gang known as Vice Society. On advice from the government and law enforcement, the district took a hard line and refused to meet the financial demands, which resulted in the release of privileged information.
Vice Society claimed it had taken 500 GB of data from the 1.6 million GB total in the system. Only a smattering has been released to date. The documents include legal and contract agreements, business records, and psychological student assessments. Though the investigation continues, initial blame for the hack has been attributed to either human error or third-party data protection failure. Luckily, school district IT techs noticed the attack was in progress shortly after it began and were able to shut it down. The LAUSD attack, which occurred in September of this year, was the 50th recorded attack on an educational target in 2022.
Retail
Thanks to the Covid-19 pandemic, retail eCommerce increased by about one-third in 2020 and has yet to look back. That muted cheer you hear is from hackers around the globe. It’s no surprise that hack attacks against retail have grown in occurrence and in the cost of remediation.
Retail is an obvious target. More than any other industry, their databases are naturally packed full of customer data like credit card info, email addresses, names, and even passwords to their online account. Typical retail cyber attack schemes include:
- Point of sale skimming
- Phishing
- Malware
- Ransomware
In deploying these types of attacks and more, a cybercriminal can impose a heavy price on a retailer that isn’t always directly measured in dollars and cents.
Impact of Cyber Attacks
The thing with a retail breach (and other industries) is that the true costs to a person whose data is stolen might not result in a true loss for years or months when their information is plucked from the Dark Web and used to steal their identity.

Here are a few recent retail breach missteps.
- A big-box store suffered a misconfigured cloud bucket and lost 300,000 sets of customer data.
- A well-known clothing retailer had 410,000 sets of personal and shipping information of customers stolen.
- An automaker suffered a breach in 2021 that affected 3.3 million car buyers.
But, on the other hand, you can’t ignore the straight-up financial cost of a breach to the average retailer. According to the 2022 IBM cost of a data breach report, the average cost of a retail data breach is $3.28 million, a slight increase from $3.27 million the year before.
Additional costs that follow a breach are:
- Making good with customers in cash payments or providing free credit monitoring
- Litigation costs in the event of a class-action lawsuit
- Breach repairs and future breach prevention
And if they didn’t before, retailers definitely have cybersecurity in mind now.
- 34% say cybersecurity is their main concern in expanding into eCommerce
- 34% of those already online say privacy breaches are the most serious digital threat they face
As for hackers, they focus on retail for these reasons.
- 99% of attackers were looking to squeeze money from victims
- In retail attacks, hackers focus on stealing payment information 42% of the time and personal identifiers 41% of the time
If you just want to take a look at straight-up costs, though, big-time breaches in recent years have ranged from $50 to $240 million (and counting). Obviously, unexpected expenses like this can create serious issues for a retail operation, including bankruptcy and closure.
Cybersecurity Initiatives
Now that we’ve unpacked a sizable amount of cybersecurity information and data from the retail industry, the obvious question is, “What will we do about all these attacks?” Cybersecurity experts have very specific programs and initiatives to suggest,
Encrypt Sensitive Data: Even if a hacker steals your data, there’s not much they can do with it if it is encrypted. It could take months or years to break into it, so they are going to go on to easier prey. Not only should data stored in a retail operation’s network or cloud servers be encrypted, but any employee connecting to the internet from a company server should use a VPN.
Segment the Network: Without wandering too far into the weeds, one big-picture strategy should be to break your network into different segments. With this arrangement, a hacker would have to successfully hack each segment to control the whole network, which is a monumentally harder task. In the event of a successful attack, the damage can be severely limited.
Data Backups: For years, cybersecurity techs have been telling anyone who will listen about the importance of data backups. Regardless of the industry, this should be a top priority. No matter the damage done by a malicious intrusion, a full backup allows you to scrub the system and rebuild it back to the most recent condition before the hack.
POS Malware: We mentioned that one of the most popular retail schemes deployed by hackers is skimming credit card numbers at the point of sale (POS). In a retail setting, in particular, dedicated POS anti-malware software is a must.
The trend toward Zero Trust Access continues to gain steam. The basic idea with this is to implement controls to your system that “trust no one”. In other words, a user has to prove themselves at every point in the system, and each time they use it. This makes it infinitely harder for bad actors to get in.
Lastly, as we’ve mentioned so many times before in this guide, educate employees, employers, and owners - anyone, in fact, who uses the network. It’s the only way to consistently thwart social engineering schemes like phishing.
Notable Cyber Attacks in 2022
We’d like to point out a few retail breaches that have happened this year, not to shame the victims (though that can be fun sometimes) but to highlight the reality of this problem. It’s not just pixels on a screen. Real companies, people, and dollars are affected.
Shein Data Breach: We like to keep these examples current, but this is a special case. For those who are unfamiliar, Shein is a fashion brand under the parent company Zoetop. The initial breach occurred in 2018 and exposed 39 million customer records.
The problem is that the breach was severely underreported. The initial admission said only around 6 million records had been stolen, and none of it contained credit card numbers. Lie and another lie. In 2022, the New York Attorney General levied nearly a $2 million fine for the misreporting.
What’s worse? Being breached or lying about it? Remember what we said about brand reputation? Reacting like this can’t help.
Rockstar Data Breach: The notorious creator of the Grand Theft Auto video games was hacked in September. The attack resulted in footage of its new version being released online. The hacker also claims to have the source code for the new game and is shopping it around to the highest bidder.
The method of entry for the breach was social engineering that came through an employee’s Slack account. This is why we spend so much time talking about employee education.
Individuals
While we’ve spent a lot of time discussing the impact breaches have on companies and organizations, let’s get personal for a few minutes. Hackers don’t only go after businesses. They don’t mind aiming an attack at an individual now and then. In general, personal IT security is one of the softest targets of all.
Impact of Cyber Attacks
Compared to breaking into a company with at least a semblance of a cybersecurity strategy, it’s typically easier and faster to penetrate a single person’s home network or personal device. Individuals wrongly assume that they are too small to draw a hacker’s attention and that it won’t ever happen to them.
The obvious facts refute that head-in-the-sand way of thinking. It can happen to you. If you’re careless enough, it probably will. There are around 4.2 billion people who use the internet for personal reasons from their homes or a variety of mobile devices.
That’s a huge pool of potential victims who aren’t convinced hackers are paying attention to them. While a minority of 44% of individuals think they might be worthwhile targets, and 86% thought they might have been phished, 40% didn’t feel confident they could tell a legitimate email from a phishing attempt.
Phishing remains super popular, but another threat vector is growing in use due to the dominance of mobile phones over desktops and even laptops. Smart hackers have figured out how to package their malware within a seemingly legitimate app and put it in the major app stores.
This Trojan horse approach successfully tricks people into downloading and installing malicious package onto their devices. What could be easier than having the victim do the work for you?
And now for something really scary. Do you use a wifi network at home? You probably do. That unfamiliar car parked down the street could be a hacker using a simple internet scanner to identify nearby neighborhood wifi networks so they can slip right in. Yes, the technology exists, and yes, hackers are doing it every day.
The ultimate impact of a successful hack on an individual is similar to a company that gets hacked.
- Stolen personal data
- Unusable device
- Costs associated with restoring it to a safe condition
The big difference is that a company will likely find it easier to recover than an individual. They have IT departments, budgets, and specialized knowledge on how to recover.
An individual is often left flailing in the aftermath of an attack, feeling violated and wondering what to do. Even worse is when you have been hacked and don’t know it, as was the case in the 2016 DDoS botnet attack that coordinated more than 100,000 individual devices in a massive attack that shut down large parts of the internet.
Cryptojackers also tend to focus their efforts on lightly-secured individual devices. So much so that attacks have risen as much as 4,000% in one quarter.
Cybersecurity Initiatives
It’s true that a company typically has more resources to recover from a hack, but an individual who finds themselves hacked has the advantage of simplicity. In other words, going forward, they only need to secure one or perhaps a few devices and maybe one home network that is likely to be much less complex than the average company network.
In other words, as an individual, you can increase your personal cybersecurity to a large degree by just taking a few simple, inexpensive actions.
Passwords: We talk about passwords a lot, and with good reason. They are the one thing that separates a hacker from the goodies. If your personal cybersecurity plan includes nothing more than good password management, you’ll be ahead of most of us.

But here are the stark facts.
- 52% of US adults reuse the same password on most of their accounts
- 13% use the same password on all of their accounts
- Only 35% use a different password on all accounts
Last but not least, a full 91% know that reusing the same password puts them at risk. But they do it anyway. Why? Not to be mean, but it could be laziness. A quick fix to this human failure is to use a password manager on your devices. This software creates and stores strong passwords and even inserts them into the login field when you’re ready to log in.
No one who goes online should be without one.
Anti-virus and Anti-malware: Here’s a secret. As long as you don’t go too far off the beaten path and buy a package no one has ever heard of, any well-known anti-virus programs are better than none.
Generally speaking, they all have similar features (see below) and cost about the same.
- Protection against browser-based attacks
- Anti-phishing protection
- Protection against viruses and malware
- Some include VPNs for encrypted browsing
The bottom line is - if you go online, you NEED anti-virus protection.
Last but Not Least - Human Error: With around 95% of all breaches attributed to human error, the solution to the vast majority of hack attacks is obvious. Stop clicking on suspicious links and downloading malicious files. Easier said than done, we realize, but even a cursory online search yields plenty of useful tips.
Notable Cyber Attack Incidents in 2022
No matter the year, you don’t have to look far to find individuals, typically high-profile, who have been hacked to one extent or another.
Liz Truss’ Phone Hack: While Truss was only prime minister long enough to say hello and goodbye, her personal phone was apparently hacked by Russian cyber agents acting at Vladimir Putin’s instruction over the summer. No details have been provided regarding how the breach occurred, but the incident points out how it’s not always the amount of data that matters.
For instance, if true, the Russians could access top secret information like private international discussions regarding the war in Ukraine, the global food and energy crises, and Truss’s opinion of how poorly the prime minister, Boris Johnson, was doing his job.
As mentioned, few details have been released, as is often the case with high-profile individuals, but you can bet any hack found was shut down pretty fast.
Twitter’s Hack-O-Rama: This incident is a tiny bit older (back in 2021) but is too good not to mention. Joe Biden, Barack Obama, and new CEO Elon Musk had their Twitter accounts hacked by a 17-year-old Florida teen. After listening to new Twitter owner Musk complain about his company’s abysmal security record, the account takeover shouldn’t come as a surprise.
The teen, Graham Clark, promoted a fake Bitcoin deal through the stolen accounts, which yielded around $100,000 and earned the youngster 30 felony counts. The cyber break-in was orchestrated using social engineering and old-fashioned phone calls. This so-called spearphishing approach convinced a number of Twitter employees to hand over access to internal tools that allowed Clark and his cohorts to conduct their scheme.
Government Institutions
Local, state and national governments have long been a target for politically and economically motivated hackers. If you want to make a splash in the day’s headlines, hacking a government agency is a good way to go about it.
But what is the actual impact of cybersecurity attacks? Do they matter, or are they just an annoyance? Yes, they are an annoyance but they can also have a substantial impact.
Impact of Cybersecurity Attacks
Amid rising political tension between the east and west (specifically the US and Russia/China), cyber attacks have become the weapon of choice. Earlier this year, the FBI issued a warning that ransomware attacks at all levels of government were straining resources and threatening to damage critical infrastructure.

There is little doubt that governments are attempting to maintain normal operations in an ever more dangerous environment that includes:
- A 31% rise in botnet attacks on corporate/government systems
- 1,136 weekly attacks aimed at the government/military
- Supply chain attacks rose by 650%, partially as a result of an increased reliance (82%) on third-party vendors
Governments find themselves especially targeted by ransomware attacks, which are launched globally at a rate of one every 11 seconds. As much as any sector, this one runs on data. Access to this data is critical to operations, which is why - despite FBI and law enforcement suggestions - governments are tempted to pay a hacker’s demand to get back online as quickly as possible.
As with breaches in the private sector, a government data breach can be a big, expensive mess. Public sector breaches have increased in both occurrences (79%) and the average cost per incident ($1.93 million).
So far, governments have fallen behind in the battle to improve cybersecurity and slow breaches. As with many other industries, the scope of the security problem wasn’t immediately recognized, and now IT teams are left in the unfortunate role of playing catch-up.
Cybersecurity Initiatives
Despite being slow to recognize the scope of cyber attacks which they found themselves under, government cybersecurity initiatives have cropped up around the globe. Here is a sampling:
- The US Department of Defense created the Cybersecurity Maturity Model Certification (CMMC). This unified standard is propagating down to 300,000 companies in the DOD supply chain.
- Spain is in the process of funding a $450 million online hacker academy project over three years - intended to attract and train talent to the cybersecurity field.
- Australia has rolled out its Critical Infrastructure Uplift Program. This project means to identify and resolve vulnerabilities in the country’s legacy computer networks through a series of specific risk mitigation strategies.
There are many more initiatives underway - too many to list. The big picture is that governments of all levels and from all corners of the earth are finally taking cybersecurity seriously.
Notable Cybersecurity Attacks in 2022
There has been no shortage of cybersecurity attacks aimed at government entities this year. Here are two worth pointing out.
Ukrainian Government and Banking Sites: At about the same time that Russia launched its live fire “special military operation,” ten Ukrainian websites related to the government and banking industry were disrupted. The culture ministry, defense ministry, foreign ministry, and two major banks were included.
The attacks took the form of a Distributed Denial of Service (DDoS) and seemed to be a continuation of Russia’s alleged cyber war against Ukrainian targets that have interfered with the operation of 70 sites since 2017. As soon as Ukraine gets one site working, another one goes down.
Pembroke Pines Ransomware Attack: Back in January of this year, the city of Pembroke Pines, FL, disclosed that it had been the victim of a ransomware attack that affected city operations and might have resulted in the theft of data from its network. With the investigation still ongoing, no specific details regarding a payout or manner of entry regarding the attack have been released. As an example of what can happen, an earlier attack on Broward county included a $500,000 ransom offered by the county, but the hackers rejected it.
Statistics on the Cybersecurity Market
We’ve arrived at the last part of the Cybersecurity Trifecta. We’ll call it the “attacks”, though it really consists of both the attacker and the defender. It is these two opposing forces that create the conflict.
You could also view this in terms of an athletic competition with teams playing offense and defense. Hackers take offense and deploy the tools and strategies at their disposal to try and compromise a target’s system. The goal is either mischief or profit.
On the other side, we have the defenders in the form of IT teams and the software and strategies they deploy to try and stop hackers from compromising their systems.
Generally, private data is the “football”. Targets have it, and hackers want it. We typically refer to these two sides as “white hat” and “black hat”.

Blackhat
The easiest way to think of a blackhat actor in terms of cybersecurity is as the one - be it an individual, organization, or country - that is willing to break into a target system and steal or compromise the private data found there.
Examples of a blackhat actor would be an individual hacker, a hacker group like Cult of the Dead Cow, or a country well-known for using blackhat tactics like Russia.
Monetization
The vast majority of cyber attacks occur for one reason - to enrich the attacker. In other words, it’s all about monetizing the activity. Much of this monetization takes place on a part of the internet known as the Dark Web. This is where stolen data is bought, sold, and traded.
The Dark Web makes up about 6% of the entire internet. It is not indexed by search engines and isn’t accessible with standard browsers. Without going down a very dark rabbit hole, the main point here is that stolen data brokers use peer-to-peer connections like TOR and I2P to navigate the Dark Web and ply their illegal trade.
The Dark Web is built on anonymity. It’s hard for law enforcement to track down who’s buying and selling all this stolen information. While it’s obviously hard to place a value on this market, estimates say it’s about $1.3 billion and growing at around 22% annually.
Markets for Malicious Software
Stolen information isn’t the only thing you can find on the Dark Web. This is also the place to go if you want to purchase ransomware or various other hack kits, from crypto mining to keylogging.
If there is something bad you want to do to someone else’s system, there’s a good chance you will find the tools to do it on the Dark Web.
Estimates say that about 2.5 million people use the Dark Web daily. It offers around 3,000 hidden websites of which around 60% buy/sell illegal products and services.
The leading nations and activities shake out like this:
- United States - 831,911 users who focus on drug transactions, fake documents, and personal identity sales
- Russia - 273,844 users head to the Dark Web for exploit kits, malware, and mass data sales
- Germany - 171,009 Germans buy/sell botnets, credit, and debit card info, and forged documents
The preceding numbers point out the reality that the Dark Web is big business and provides a thriving profit opportunity for those who are so inclined.
Selling Trade Secrets and Sensitive Customer Data
The numbers tell the tale when it comes to selling stolen information online. Even though data breaches were down by 56% in the second quarter of 2022, a tribute to a renewed global focus on cybersecurity, there were still 52 million breaches, each one a chance for the hacker to sell the harvested data for profit.
How much is stolen data worth on the Dark Web? Here are some examples.
- Social security number - $1
- Credit/debit card - $5 to $110
- Driver’s license - $20
- Passport - $1,000 to $2,000
- Medical records - up to $1,000
While some of these prices might seem modest, consider that an individual hacker could snag millions of records with a single breach. It’s easy enough to post what they have for sale to the Dark Web and wait for an interested shopper to stop by.
For business breaches where trade secrets were stolen, anonymously offering them to competitors is a frequent tactic.
Acquiring Traffic or Ad Views
An entire industry has grown up around stealing ad revenue and redirecting online traffic. There are a variety of ways in which these types of scams play out, but here are a few examples.
- February 2020 saw Google delete 600 apps from its app store as punishment for sending false impressions to their own ads.
- Click spam involves software that automatically generates clicks to competitor ads and runs up illegitimate ad spending.
Bad bot traffic is another scheme that costs billions every year. Paid search and social campaigns find themselves under almost constant assault to the tune of $3.8 billion lost in e-commerce.
The eLearning industry also suffers heavy losses, logging $2.6 billion to click fraud and another $830 million annually to malicious bot traffic.
As you can see, hackers skilled in the somewhat esoteric arts of generating fraudulent clicks and other marketing shenanigans stand to earn a lucrative living.
Nation-State Sponsored Attacks
Real war that involves actual humans, machinery, and weapons is expensive. At some point in the internet’s evolution, smaller nations that lacked the budget for launching traditional offensives turned to cyber attacks.
With just a handful of skilled IT techs skilled in blackhat arts, an alarming amount of damage can be inflicted on a much larger and more affluent nation. The numbers bear out the fact that the popularity of this kind of attack is increasing.
A recent study found a 100% increase in nation-state attacks from 2017 to 2021. Let’s take 2020, a year in which there were 20 attributed attacks. Physical targets played a role in 40% of the targets - for example, infrastructure associated with public utilities.
In a departure from typical breaches perpetrated by individual hackers on private interests, nation-state hacks tend to focus on creating damage or destruction in 14% of the cases, with data theft only a goal 8% of the time.
Interestingly, modern attacks have shifted from focusing on government cyber agencies (25%) and other government organizations (12%) to targeting large corporations (35%).
Emerging studies have found a definite connection between sponsored attacks and organized crime. Perhaps this is the reason that attacks are not evolving into more advanced techniques but relying on tried and true and relatively basic tools.
To summarize our blackhat discussion, hackers who fall into this category have no compunction about breaking into computers and networks with malicious goals to do things like destroy or encrypt files, steal personal information, or even just create chaos for its own sake.
These are the bad guys of the online world.
But there are two sides to every coin. Let’s take a look at whitehat or ethical hacking networks
Whitehat (Ethical Hacking)
Blackhat hackers are the ones that garner the vast amount of media attention, but there is a thriving community of people with the same skill set but who ply their trade for the public good. These are whitehat hackers.

The typical role for a whitehat hacker, whether it’s an individual, private security firm, or larger government agency, is to locate exploits or vulnerabilities in programs or systems before the community of blackhats do and sound the alarm.
They do this by approaching a system as of they were trying to compromise it.
This testing function is critical to shutting down code backdoors before one of the bad guys finds it. Security firms, government agencies, and businesses may all hire ethical hackers.
Bug Bounty Programs
Ethical hackers earn a living by participating in bug bounty programs. This is exactly what it sounds like. Businesses or any other entity that develops software or hardware offers a financial reward for any code failures (exploits, vulnerabilities) discovered that relate to security.
When we say a financial reward, we’re not talking about chump change for the Taco Bell Happy Hour drink special. Take a look.
- Crypto-exchange Binance pays up to $100,000 for bug reports
- Kraken’s minimum payout is $500
- Crypto.com payouts range from $1,200 to $80,000
The use of ethical hackers is growing. A full 24% of internet and online service companies now offer some level of bug bounties. Software companies aren’t too far behind at 16%, while financial services come in at 8%.
Additionally, more than 7,000 whitehat hackers are on the bug bounty platform Hackenproof.
Even the government is getting in on ethical hacking action. The Department of Homeland Security pays from $500 to $5,000 for novel vulnerabilities found on their site.
When it comes down to the bottom line, it makes sense to pay the good guys to try and stop the bad guys. Expect the whitehat industry to continue to grow roughly in line with the blackhat one.
Career Opportunities
It used to be that a company would just grab someone from the IT team and designate them as the “security specialist”. Chances are they had not been given any special training and didn’t have a security-oriented education.
The problem with this approach is obvious, and blackhat hackers were only too eager to exploit it. Over the years, cybersecurity has evolved to the point where a whitehat hacker can enjoy job opportunities and an actual career path while specializing in ethical hacking.
The whitehat industry stands at about $170 billion. With 68% of business owners thinking that cybersecurity risks will only increase in the future, expect the sector to keep growing. Employment opportunities with any of the following organizations are wide open.
- Government
- IT sector
- Law enforcement
- Intelligence agencies
- Financial institutions
- Individual companies
- Security agencies
How much do ethical hackers make? Estimates range from $50,000 to $100,000 for a newbie. Seasoned veterans can command more.
Cybersecurity has been a high-growth field since 2017 and shows no signs of slowing down.
Contractor Opportunities
Sometimes you don’t want a full-time job working for a single company. The Covid-19 pandemic supercharged the gig economy, and there are plenty of ethical hackers making a good living as a contractor rather than employees.
In general, freelance work has been growing like crazy around the world. In the US alone, there are around 57 million freelance or contract workers, and freelancing has been growing for a while. Throwing out 2020 as an outlier due to the pandemic, 28% of the US population now freelances full-time. This slow, steady growth is up 17% since 2014.
With the global gig economy projected to hit $455 million by the end of next year and with those in the cybersecurity sector towards the high end of the pay scale, now might be a good time to make the leap.
There are a variety of freelance platforms dedicated to helping giggers find work and different ways to go about it. Some prefer to go it alone and slowly build up a clientele one at a time. Others choose to form a consultancy agency with other ethical hackers and follow that business model.
One thing is certain. Any career related to cybersecurity is hot right now.
Cybersecurity Industry Forecasts
The cybersecurity industry is growing. Fast. There are a handful of reasons that began to be felt in 2017 and right now have developed into the perfect storm: blackhat hacker sophistication, the Covid pandemic’s push towards remote work, the growth of lightly-secured mobile and IoT networks, and a ho-hum attitude towards security.
Meanwhile, hacks and breaches continue unabated. But what cold hard numbers does the cybersecurity industry have to show us?
Threats and Types of Attacks
As we’ve seen through the course of this article, hackers deploy several different attacks to pursue their criminal goals. Each requires a different skill set though some are similar. Some are perenially popular and others less so.
Here’s what we can expect in the near future when it comes to the frequency of cyber-attacks.
Malware: This catch-all term refers to a variety of attack software like viruses, rootkits, trojans, worms, ransomware, adware, spyware, and the list goes on. Successful malware attacks tend to cause the most financial damage to a target, but the number of attacks has been declining in recent years. That trend is expected to continue.
Security experts credit better malware and a higher level of cybersecurity awareness on the part of the general public. Currently, there are around 700 malware attacks per week, but that number is expected to decline in the future.
Ransomware: Unlike malware, ransomware has been increasing since 2015 and shows no signs of slowing down. Ransomware hits a business every 11 seconds, and average damages have increased almost 300% while the annual cost of remediating these attacks stands at $20 billion annually.
Paying the ransom doesn’t appear to help the chances of recovery. Often, it simply results in a second infection of your system from the same group. Thanks to hacker success with the technique, expect ransomware to continue to grow in popularity.
Phishing: Phishing is a term that refers to the use of social engineering techniques to trick targets into downloading a malicious file or clicking a dangerous link. This old reliable form of cyber attack has remained popular because it is based on human nature, and it works.
Around 5% of all emails sent are phishing attempts, and 38% of all cyber-attacks are phishing. Expect this one to experience steady growth into the future.
DDoS and the IoT: A successful DDoS attack requires that a hacker assume control over hundreds or even thousands of internet devices. It’s not the simplest attack but thanks to the low level of security of the growing Internet of Things (IoT), it is now within the reach of more hackers.
DDoS attacks are expected to hit around 14 million annually by the end of this year. A recent increase in spending on IoT security ($3 billion in 2021) will likely make it harder to carry out widespread successful attacks like this in the future but don’t expect them to go away completely.
Cryptojacking: Cryptojacking only accounts for 2.5% of all cyber attacks. It didn’t even exist until about ten years ago when cryptocurrency came on the scene. With cryptocurrency itself still a bit of a wild card as far as its long-term survival and value, cryptojacking finds itself in the same category.
Cryptojacking grew by 163% in one quarter alone recently. If it keeps that up, expect it to be a player in the cybersecurity game going forward. But if the bottom happens to drop out of the digital currency market, cryptojacking will become nothing more than an interesting memory.
Though a handful of reliable threat vectors stick around from year to year, there are new ones that arrive on the scene and old ones that go. That’s what makes life interesting.
Check back in a year, and we’ll see how good our predictions were.
Targets of Cybersecurity Attacks
Unless you never go online, in which case you’re probably not reading this, there aren’t too many people who aren’t a target of cybersecurity attacks to some extent. Hackers go after individuals, small, medium, and large-sized businesses, governments, public utilities, schools, and universities.
If there is private data or information involved, expect that a hacker will eventually take a shot at it. That’s where a proactive approach to cybersecurity works in your favor. If your system is secure and they can’t get in, they’ll likely move on to an easier target.
Having said that, anyone can be a target, there are some sectors of the economy that hold what is perceived by the bad actors to be higher-value information. We’re talking about healthcare, the financial services industry, and government agencies.
Impact of Cybersecurity Attacks
Thanks to the pandemic and its aftermath, making cybersecurity predictions for the past two years has been a challenge. Still, stalwart industry leaders weren’t afraid to talk to the Center for Internet Security and take a guess at what 2023 holds in store.
Here are some of their ideas.
- In a perennially understaffed industry, cybersecurity professionals will begin to address their workers' mental and physical health.
- Cyber attacks on physical assets will increase. Think the Colonial Pipeline, the Oldsmar water-poisoning scare, and the JBS Meatpacking Plant.
- Software developers become the target of ransomware. Holding new products hostage in the midst of development might be the most lucrative use of this technique to date.
- Increased automation, baked-in security, and simplified management.
- Widespread adoption of endpoint monitoring, multi-factor authentication, and zero trust access strategies.
Like breathing and taxes, cybersecurity is with us to stay. What was a minor concern in the early days of the internet has evolved into a full-fledged Big Deal. If you don’t agree, try ignoring it for a while. Remove all anti-virus and anti-malware from your system. Turn off your VPN. Visit unsecured sites. Click on suspicious links. Go wild!
We’d guess you will have about five minutes of unfettered freedom from cybersecurity before your device is so infected you have to take it out and shoot it. The bottom line is - cybersecurity matters. A lot.
Cybersecurity Initiatives
Back in January of this year, a cybersecurity outlook report was issued at the World Economic Forum. While certainly not a policy statement for the world, it did point to major trends and future challenges we all face.
Cyber Resilience: The first big concept for successful future cybersecurity is designing cyber resilient systems. This means that an organization is able to carry out its mission even as cyber-attacks are in progress. Currently, 59% of cyber leaders don’t see a difference between cybersecurity and cyber resilience, and only 17% are confident that their systems are cyber resilient.
Going forward, this is a catchword and reality - everybody needs to get cyber-resilient!

New Sophistication: There’s no doubt that technology is quickening. In other words, new and more advanced products and services come around ever faster. Cyber attacks are no exception. The attacks of ten and twenty years ago seem like stone knives and bear skins now.
The new normal is a frequency and level of sophistication that has not been seen in data breaches before.
Take a look at the amount of new data one minute of internet time brings to us:
- 28,000 Netflix subscribers watching
- 695,000 Instagram stories shared
- 9,132 new LinkedIn connections
- 69 million WhatsApp messages sent
- 5,000 TikTok downloads
- 500 hours of YouTube content uploaded
- 197 million emails sent
- $1.6 million spent online in the US
You get the idea. The amount of data to be protected is unimaginable unless you have a really big brain. It has grown beyond human comprehension. What can we do? Don’t look now, but AI is coming to the rescue and will have a lot to do with the future of cybersecurity.
Talk to Each Other: There is an unfortunate trend in place right now that is illustrated by a disconnect between the business leader of an organization and the security leader. This is like trying to juggle when the right hand doesn’t know what the left is doing and vice versa.
And the gap is widening.
Going forward, there are some ideas to put into practice.
- Prioritize security in business decisions
- Co-equal leaders learn to support one another
- Recruit and retain talent that understands the big picture
Here are a set of statistics that represent the disconnect. 41% of business executives believe that cyber resiliency is an already established business priority. Only 13% of security executives believe the same thing.
‘Nuff said.
Cybersecurity Market
Did we say the cybersecurity market is growing? In case not, we’ll do it now - the cybersecurity market is growing. From an estimated value of $176 billion in 2020, it is projected to climb to $403 billion by 2027.
Add to that the fact that 66% of organizations expect to have a larger security budget over the next few years. A full one-third anticipate a double-digit increase. Now that’s a trend that matters. Perhaps the best indication that a company is taking cybersecurity more seriously is when they spend more money on it. Here are some examples of that in action.
- Google is throwing its hat into the cybersecurity ring, announcing that it will spend $10 billion by 2025 to advance open-source security, zero-trust programs, and the software supply chain.
- Congressional spending on the federal level shows congress agreeing to add $15.6 billion for cybersecurity into the 2023 budget.

With companies facing a 31% increase in cyber attacks since 2021, the need for effective resilience and remediation strategies has never been more urgent. We’re going to guess that everybody with an iron in the fire and a checkbook in their pocket will start scratching checks.
From the individual who buys a new anti-virus software to the international company that fortifies its entire edge computing interface, people will get more serious about cybersecurity than ever.
The Bottom Line
This has been a long article, and we don’t blame you if you stopped for a nap or caffeinated beverage along the way. For those who stuck with us all the way through, you can pick up your door prize valued at $100. Just kidding. There is no door prize.
But you did get a thorough review of today’s cybersecurity environment through the lens of the Cybersecurity Trifecta - the attacked, the attackers, and the attack. That probably makes much more sense now than it did at the beginning.
The real bottom line is that a basic understanding of cybersecurity and how to implement it in your situation is no longer optional. Well, actually, it is optional, but it’s a bad idea not to take it seriously.
Most of us have put a significant part of our lives online. We can suffer real losses if we don’t take steps to protect it.
FAQ
What is the likelihood of being hacked?
The varied nature of the internet, hackers, and defensive systems makes it difficult to come up with a single solid percentage. One super-conservative study put the risk at .32%. Another concluded that approximately one out of every two companies gets hacked, so it must be 50%. So our answer is this. No one knows, but you better be ready when it happens.
How common are cyber crimes?
More than 600,000 Americans fell victim to a cyber crime in 2021. Financial losses were estimated at $4 billion.
How big is the cybercrime market?
FBI estimates say that the cybercrime underground economy is around $114 annually, though that total comes with many unknown variables.
What is the biggest data breach in history?
The largest breach in history happened in March of 2020 to the adult video streaming website CAM4. Almost 11 billion records were exposed that contained THE most sensitive of information: full names, email addresses, sexual orientation, and chat transcripts, to name a few.
How much malware is created every day?
Every single day, around 450,000 new malware infections are logged. That’s a bunch.
